 The Illuminati (or Moriah Conquering Wind as they prefer to call themselves these days) is a very secretive group of occult practitioners who have been around for thousands and thousands of years. It is not a boys' club or a group of adults parents trying to get some excitement in life; this is something much bigger than that. This is a very well structured organization consisting of people in extremely High Places. Those people are the Super Wealthy, who stand above the law. Many of them don't even appear on the list of the wealthiest people in the world - it's that secret.
The Illuminati (or Moriah Conquering Wind as they prefer to call themselves these days) is a very secretive group of occult practitioners who have been around for thousands and thousands of years. It is not a boys' club or a group of adults parents trying to get some excitement in life; this is something much bigger than that. This is a very well structured organization consisting of people in extremely High Places. Those people are the Super Wealthy, who stand above the law. Many of them don't even appear on the list of the wealthiest people in the world - it's that secret.
THE ILLUMINATI AND THE BLACK NOBILITY
The word Illuminati means 1. People claiming to be unusually enlightened with regard to a subject. 2. Illuminati Any of various groups claiming special religious enlightenment. Latin ill mi
mi t
t , from pl. of ill
, from pl. of ill min
min tus, past participle of ill
tus, past participle of ill min
min re, to light up. Seeilluminate. These definitions are taken from "The American Heritage Dictionary of the English Language".
re, to light up. Seeilluminate. These definitions are taken from "The American Heritage Dictionary of the English Language".
Those people are the top players on the International playground, basically belonging to the thirteen of the wealthiest families in the world, and they are the men who really rule the world from behind the scenes (yes, they are mostly men, with a few exceptions). They are the "Black Nobility", the Decision Makers, who make up the rules for presidents and governments to follow, and they are often held from public scrutiny, as their action can't stand being scrutinized. Their bloodlines go back thousands and thousands of years, and they are very careful with keeping those bloodlines pure from generation to generation. The only way to do so is by interbreeding.
Their power lies in the occult and in economy - money creates power. The Illuminati own all the International banks, the oil-businesses, the most powerful businesses of industry and trade, they infiltrate politics and they own most governments - or at least control them. An example of this is the American election for presidency. It is no secret that the candidate who gets the most sponsorship in form of money wins the election, as this gives the power to "un-create" the opposed candidate.
And who sponsors the "right" candidate? The Illuminati do. More often than not they sponsor both sides to have a game going. They decide who will be the next president, and they see to that their man wins, even if they have to cheat like they did in Florida when President George W Bush "won" over Al Gore. Most president campaigns are financed with drug money, which is understandable if you know that the Illuminati run the drug trade industry as well. Elections are really not necessary, but they let us vote so we can have a game, and by letting us, they pretend to follow the Constitution.
But is the President really running the game? Not the least. The power does not lie with the politicians, but with the Illuminati, whose top members are mostly International Bankers. The leading candidates for Presidency are carefully chosen from the occult bloodlines of the thirteen Illuminati families, and if we research all the Presidents of the United States from the beginning and up to now, we will see that almost all of them are of the same royal bloodline, and they are all "family"; related by ancestry and family trees. Royalty is equivalent to the Illuminati.
So what are the goals of the Illuminati? To create a One World Government and a New World Order, with them on top to rule the world into slavery and fascism. This is a very old goal of theirs, and to understand it fully, one must realize that this goal isn't of a kind that's supposed to be obtained within one lifetime - it has been a goal that slowly is to be accomplished over a long period of time. However, they have accomplished more in this direction during the last few decades than they have done in hundreds of years due to industrialization and the Information Technology Era. Their immediate task is to lower the living standard of the developed countries, like the United States and Europe, to a low enough level, so the government can more easily control us (you can see this happening). The living standard in the third world countries will increase to the low level that is planned for the developed countries, so that all levels out. To be able to accomplish a New World Order, the living standard must be similar all over the world. You can see this happen right now. The following article shows it clearly: Africa and Asia Push for 'New World Order'.
 This goal has been planned away from the public's prying eyes, in secrecy within the Secret Societies. All Secret Societies with secret grades of initiation are owned and controlled by the Illuminati, and Freemasonry is maybe the best known. The persons who control the societies and the Illuminati are occultists and black magicians. Their God is Lucifer. "The Light Bearer", and by occult practices they manipulate and influence the masses. It doesn't matter if you and I believe in this or not, as long as they do. And they take it very seriously.
This goal has been planned away from the public's prying eyes, in secrecy within the Secret Societies. All Secret Societies with secret grades of initiation are owned and controlled by the Illuminati, and Freemasonry is maybe the best known. The persons who control the societies and the Illuminati are occultists and black magicians. Their God is Lucifer. "The Light Bearer", and by occult practices they manipulate and influence the masses. It doesn't matter if you and I believe in this or not, as long as they do. And they take it very seriously.
It's a thrilling thought, that this planet as a matter of fact is run with Black Magic - a planet where magic is not supposed to exist at all in any shape and form, except in the movies and in books, and if somebody tells you it does exist, he/she will most certainly be ridiculed. After people have watched movies like "Lord of the Rings" they wish there was more magic in their lives; little do they know ...
From the occult, mind control and Intelligence have developed. By taking over the Movie Industry, the Record companies, and by their control of the Fine Arts, they know how to influence the teenagers to dance to their own tune and accept their kind of reality. This makes sense if you look at what kind of "entertainment" we are enforced to enjoy.
The music the teenagers have to listen to is often totally without quality and lead them into "robotism", apathy, violence and drugs. It's also used for mind control, as we shall see later. Real quality music is rejected by the big record companies in favor for those with lack of talent. Since Black Sabbath in the beginning of the 70:s and the Rolling Stones before them, occultism and Satanism has been promoted through the music industry. Many groups followed on the same track and have always been Hard Sale and heavily promoted and distributed.
The same thing goes with Hollywood, which is also controlled and created by the Illuminati. The "E.T"-movies, Dooms Day films and catastrophe-movies all align with the purpose to influence us in certain directions. Occult movies have also been made popular. All to prepare for days to come ...
I told you above that the men who control the Illuminati are members of thirteen wealthy families. Who they are have been a well hidden secret, and the leadership has gone from man to man over generations. Nevertheless, no secrecy is kept forever, and sooner or later there will be leaks, so also in this case. Not many people know who these families are exactly, but quite recently this has become known, due to people from Illuminati who have left the Order and revealed the most remarkable data. So here are the names of the 13 families - the Secret Government
1. Astor
2. Bundy
3. Collins
4. DuPont
5. Freeman
6. Kennedy
7. Li (Chinese)
8. Onassis
9. Rockefeller
10. Rothschild
11. Russell
12. van Duyn
13. Merovingian (European Royal Families)
The following families are also interconnected with those above:
1. Reynolds
2. Disney
3. Krupp
4. McDonald
Also, in addition to those four families, there are hundreds of others that are connected more distantly to the main 13 Illuminati bloodlines. Although significant, they are not mentioned here; they are considered less powerful and less pure by the 13 Elite Bloodlines.
 All the families above can be studied in much more detail in Fritz Springmeier's excellent book: "Bloodlines of the Illuminati".
All the families above can be studied in much more detail in Fritz Springmeier's excellent book: "Bloodlines of the Illuminati".
SECRET SOCIETIES

The Secret Societies have been present in the history of man for a very long time. It all started thousands of years ago with the "Brotherhood of the Snake", a secret society that refers to Satan (the Great Serpent) back in the Gar
den of Eden. The Illuminati consider Sata
n being to good God and the Old Testament God to be evil. Their opinion is that Satan gave man knowledge, while God tried to suppress the same. From this viewpoint Satanism was developed and is practiced within the secret societies up until this day.
There are different theories as of where the secret knowledge within the secret societies comes f
rom, and I am going to mention the two most common theories:
In the Sumerian Scriptures, which go back at least 6000 years, the stone tablets tell us about the 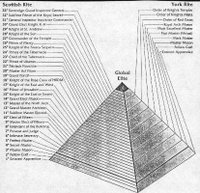 Anunnaki "they who from heaven came". According to researchers like Zachariah Sitchin, David Icke and William Bramley, the Anunnaki were the Gods mentioned in the Old Testament of the Bible, and they were aliens who came from another planet and created humankind as a slave race to serve them. The Sumerian Scriptures tell us about Anu, who was the king of the Anunnaki, and Ea (or Enki),
Anunnaki "they who from heaven came". According to researchers like Zachariah Sitchin, David Icke and William Bramley, the Anunnaki were the Gods mentioned in the Old Testament of the Bible, and they were aliens who came from another planet and created humankind as a slave race to serve them. The Sumerian Scriptures tell us about Anu, who was the king of the Anunnaki, and Ea (or Enki),
who is equivalent to S
atan. He is told to be the one who gave the knowledge to man in the Garden of Eden, and created the first secret society, the above mentioned "The Brotherhood of the Snake". The Anunnaki is said to have come here to exploit the resources of the Earth; especially gold, as this was something they were lacking on their planet, and they urgently needed it as an important ingredient in their atmosphere. Thus Ea, who was a brilliant scientist, created homo sapiens as a hybrid betw
een a primitive earth life-form and the alien race.
(NOTE: If you, the r
eader, have a problem accepting the alien part of this agenda, feel free to exclude it from the picture for now, and please continue to read. You will most certainly find the evidence overwhelming on this website with- or without the alien involvement. The truth speaks for itself. However, if you still wa
nt to research the alien/interdimensional part of it all, I suggest you visit the Disclosure Project Website and watch The Disclosure Project Video. Approximately 500 government employees testify about the alien agenda and that the aliens are among us, and they are all willing to go to court to testify further, in
public. This video definitely convinced me, and many many others who were 100% sure the alien agenda was a piece of disinformation. Please continue to be skeptical while watching this video and exploring the website, but don't be skeptical beyond reason. The same goes for the information on this website of mine. The full testimonies of those 500+ governme
nt people are gathered in the book "The Disclosure Project", which can be ordered from their website. In the book are also actual classified documents, and tons of those can also be found at the Disclosure Project Website).

Enki (Ea) is sitting on the chair to the right
First homo sapiens were only meant for slave labor and couldn't breed. Later on this was changed. Although Ea didn't like how his created race was treated as an inferi or race , he wanted to enlighten them by teaching them who they were and where they came from. He also wanted to tell them the well hidden truth that each individual is a spirit inhabiting a body and that after body death the spirit lives on and rein
or race , he wanted to enlighten them by teaching them who they were and where they came from. He also wanted to tell them the well hidden truth that each individual is a spirit inhabiting a body and that after body death the spirit lives on and rein
carnates on Earth.
David Icke, who has researched the Illuminati for decades, claims that the top Illuminati bloodlines are shape shifting reptilians, aliens not from space, but from another dimension, and that THEY actually are the Anunnaki "Gods". According to him, they are the ones in charge of the secret societies. Those entities have the ability to shape shift into human form, and he says he has hun
dreds of witnesses who have seen them shape shift back into reptilian form.
The Christian viewpoint on this is that the Anunnaki in fact were the Giants that walked the Earth, which the Bible is talking about. Those Giants were the nephilim, who rebelled towards God and were cast down to Earth from Heaven, together with their master, Satan. Christians explain the shape shifting theory by saying that the aliens in fact are demons and the nephilim. They mean that the persons that have been seen shape shifting are merely demon possessed due to their black magic practices, and sometimes the demons "bleed through" and show themselves, either in reptilian form or as the "grey aliens". Maybe the different conclusions are just different interpretations of the same thing?
Whatever the truth is, there is definitely something going on. There are too many witnesses, and in the era of the Internet it is easier for people to communicate world wide. This may be the reason why we hear so much about this phenomenon now, where there once was silence. There is no Media cover-up on the Internet. On the other hand, we cannot take everybody that steps forward on the Internet seriously, as things like these also can create psychological chain reactions. Some people may "believe" they have experienced something that they actually haven't. This is not meant to be a religious web site, so I will not argue too much about these things; especially as I don't have the answers myself. On the contrary, this site has as one of i
ts' purposes to explain the world situation from an objective viewpoint - as objective as possible.

The truth is; in the background throughout all history there are secret societies. The original Brotherhood soon split up in cults, when certain people on top were in disagreement with each other. Different powers of control developed, where they fought against each other internally (which still is the case today), out of sight from an ignorant population. They invented the different religions and sects and cults so man would be busy doing something else instead of looking into what the Brotherhood actually was doing. They put themselves in charge of the churches to entrap people and to spread conflicts between different belief systems. Most wars throughout history have been religious wars.
Out of the original Brotherhood came Freemasonry, the Rosicrucians, The Knight Templars, Ordo Templi Orientis, Knights of Malta and more. Some people may object and say that Freemasonry, for example, is a charity organization and even a Christian society. Yes, that's what we're told and that is what most members of the secret society believe. The vast majority of people involved are good people, who are ignorant of what is practiced on the highest levels; unaware of that up there is Satanism and worship of the dark forces. They don't serve God, they serve Satan or Lucifer, and this is the key to what is happening in the world of today.















































